
Newsletter Subscribe
Enter your email address below and subscribe to our newsletter

Here’s the thing about scammers: they’re lazy. They’ve always been lazy.
In the past, that meant laughably bad grammar in emails (“Dear Esteemed Sir, kindly send me your Social Securitys”).

Now? They’ve outsourced the work to Artificial IntelligenceArtificial Intelligence (AI) is basically when computers get smart—really smart. Imagine if your c... More.
Which means instead of getting caught by typos, you’re staring at an email that looks like it came straight from your bank’s fraud department. Or a voice on the phone that sounds exactly like your son asking for money. Or documents so polished they’d pass a DMV eye roll test.
Welcome to the new age of identity theft, where the crooks are armed with supercomputers instead of crowbars.
Scary? Yes. Unstoppable? No.
The crooks may have upgraded their toolkits, but you’ve got something better: common sense, a skeptical eyebrow, and a few easy habits that can keep your identity where it belongs — with you.
Let’s dig in and learn how you can keep you and your loved ones safe from AI identity theft.
Think of AI identity theft as the same old scams—impersonation, forgery, and good old-fashioned lying—wearing a brand-new, shockingly realistic mask.
Instead of a poorly written emailEmail, or electronic mail, is a digital communication tool that allows users to send and receive mes... More from a “Nigerian Prince,” you get a perfectly crafted message from your bank or a video call from a loved one that looks and sounds real.
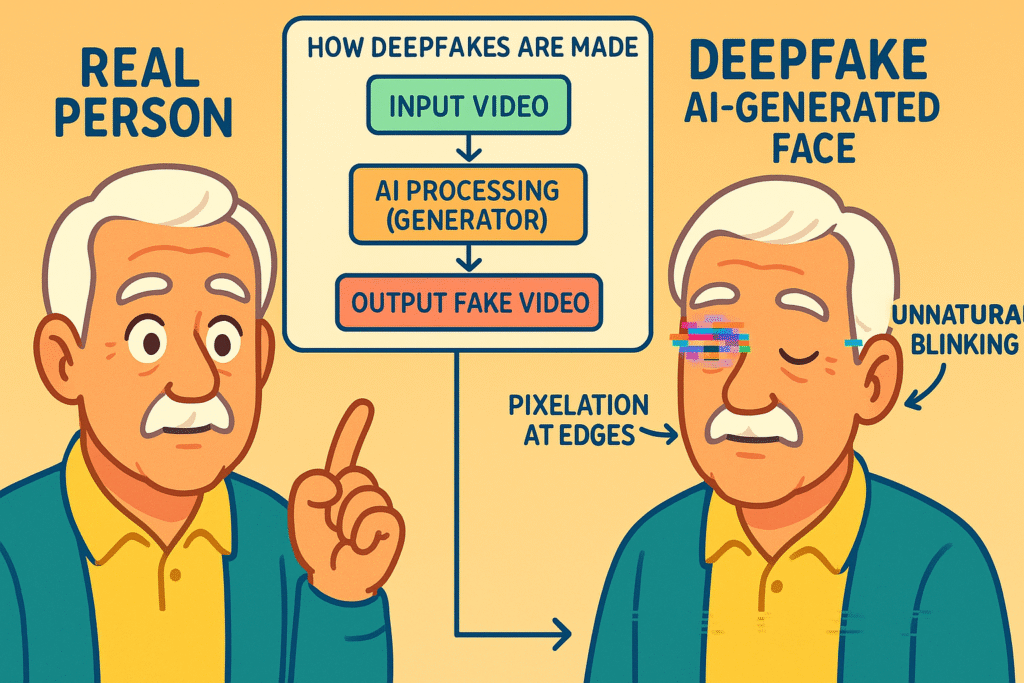
The word “deepfake” sounds like something from a sci-fi movie, but the concept is surprisingly simple. It’s a term for realistic fake video or audio created by AI.
Imagine you have two super-smart computers.
The first computer, let’s call it “The Forger,” studies thousands of pictures and videos of a person—say, your favorite movie star.
It learns every angle of their face, how they blink, and the sound of their voice. Then, it starts creating fake videos of that star saying things they never said.
The second computer, “The Detective,” looks at The Forger’s work and tries to spot the fakes.
The two computers go back and forth, millions of times, with The Forger getting better at fooling The Detective, until the fake becomes nearly impossible to spot.
That’s a deepfake. It’s a digital puppet that can be made to do or say anything.
This tech isn’t just for video. Scammers are now using AI to create flawless fake documents.
They can generate a driver’s license with your name and someone else’s picture that looks 100% official.
They can create fake bank statements, utility bills, or even forge your signature on a digital contract so perfectly that it would fool a handwriting expert.
This is a huge leap from the days of fuzzy, photocopied fakes. AI can create documents from scratch that look crisp, legitimate, and ready to be used to open a new credit card in your name.
Criminals are lazy. They use these powerful tools to run the same old plays, because unfortunately, they still work. Here are the most common ways AI is being used in scams.
As we mentioned, scammers only need a few seconds of a person’s voice to create a convincing clone.
Where do they get it? A public video on Facebook, a cheerful voicemail greeting, or even a clip from a local news story.
They use this cloned voice to call you, pretending to be a family member in a desperate situation, counting on your love and panic to make you act before you think.
Remember those scam emails filled with typos and awkward grammar? Those were easy to spot.
AI, however, is a grammar nerd. It can write flawless, personalized phishingPhishing involves cyber thieves creating fake communications, often appearing as emails from trusted... More emails that look exactly like a real fraud alert from your bank or a shipping notification from Amazon.
They might even reference a recent purchase to seem more legitimate, tricking you into clicking a dangerous linkA link, or hyperlink, is a tool used in electronic documents and websites to jump from one online lo... More.
This one is sneaky. Instead of stealing your entire identity, scammers create a synthetic one.
They take a real piece of information, like your Social Security number, and combine it with completely fake details, like a made-up name and address.
They use this “Frankenstein” identity to apply for loans or credit cards. Since the name is fake, the denial letters don’t come to you.
The scammer builds up the credit of this phantom person for months before maxing out all the accounts and disappearing, leaving a mess that’s tied to your good name.
This all sounds terrifying, I know. It can feel like we’re living in an episode of The Twilight Zone.
But here’s the good news: the most powerful defense you have isn’t a fancy piece of software. It’s your own common sense, powered by a healthy dose of skepticism.
Even the most advanced AI scam still relies on one thing: emotional manipulation.
They want you to feel scared, rushed, or excited. They create a sense of urgency—”You have to send the money now!”—so you don’t have time to think.
If a call, email, or text message makes your stomach clench, that’s your built-in fraud detector going off. Listen to it.
If you get a frantic call from a loved one asking for help, stay calm and do this: Hang up and call them back on the number you know is theirs.
No matter what they say (“My phone is broken!”), hang up and call their real number.
For an even better defense, agree on a family “safe word” or a silly question that only you would know the answer to.
Something like, “What was the name of our crazy Uncle Larry’s poodle?” A scammer won’t have a clue, but your real grandson will.

Even the best deepfakes have “tells” if you know what to look for.
Scammers use the information you share online as the raw material for their fakes. Every public photo, video, and personal detail is another tool for them.
The best defense is to reduce what they have to work with. Go through your social mediaSocial media refers to online platforms and websites that enable users to create, share, and interac... More accounts and tighten your privacy settings.
For example, on Facebook, you can limit past posts facebook has stored so that only friends can see them. Think twice before posting a video where you clearly state your name or other personal details.
It’s when criminals use Artificial Intelligence to create highly convincing fake videos, voices, text, and documents to impersonate you or someone you trust, with the goal of stealing your money or personal information.
Look for visual oddities like unnatural blinking, blurry edges, and weird lighting. Listen for a robotic or emotionless tone, strange pacing, and a lack of background noise. Most importantly, if the message is urgent and asks for money, assume it’s a scam until you can prove otherwise.
First, don’t engage. Hang up the phone or delete the email. Don’t click any links. Second, try to verify the situation by contacting the person or company through a separate, trusted channel (like a known phone number or official websiteA website is a collection of interconnected web pages or digital content that are accessible via the... More). Finally, report the scam attempt to the Federal Trade Commission (FTC) at ReportFraud.ftc.gov.
Absolutely! Strong, unique passwords and two-factor authentication are more important than ever. They act as a critical line of defense if a scammer tries to take over your accounts after tricking you.
They scrape it from public sources: social media profiles, online videos, company websites, data breaches, and any other place where your name, voice, or image appears online. The less you share publicly, the safer you are.
Navigating this new digital world can feel like a chore, but protecting yourself boils down to a few simple, timeless habits.
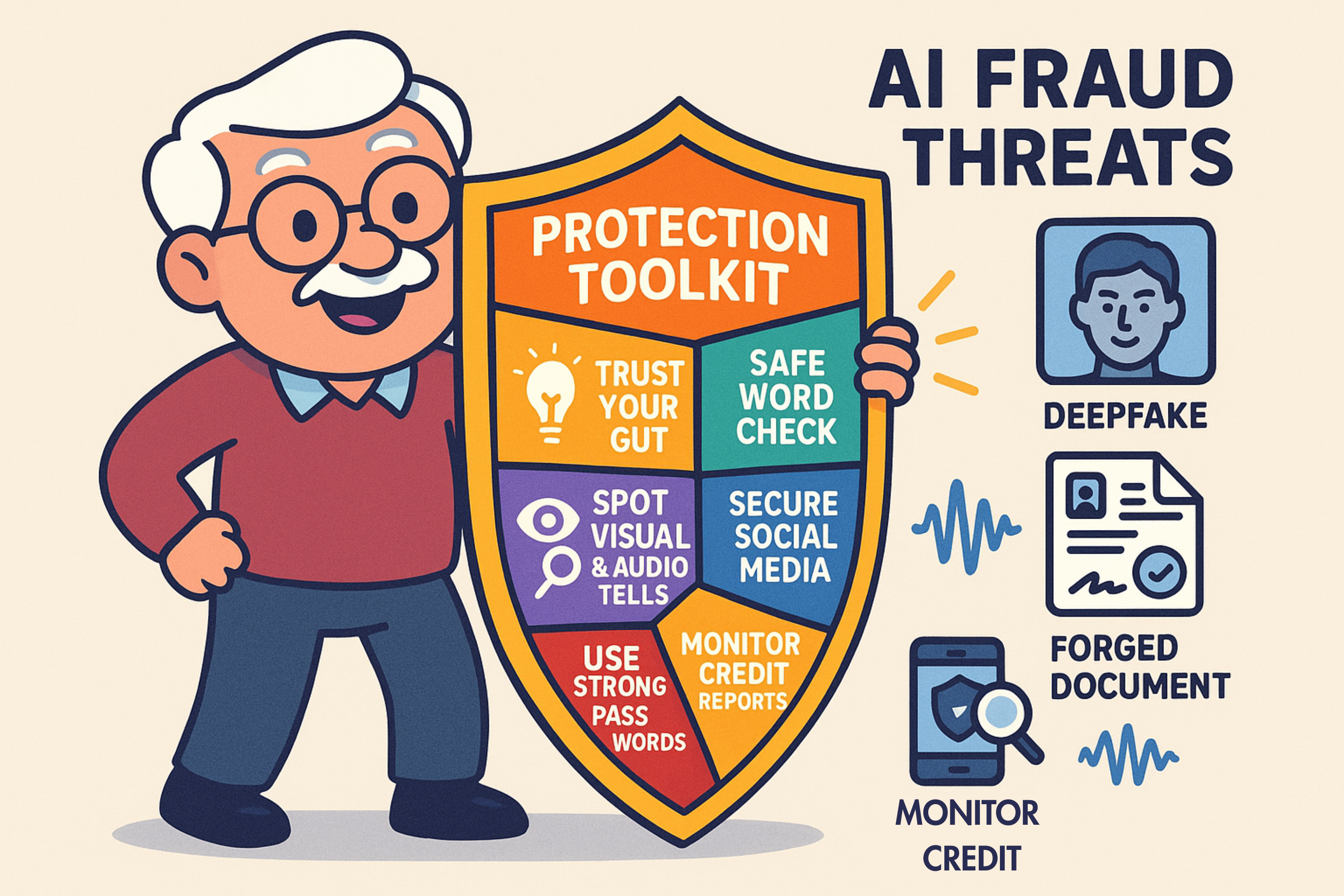
Technology will always change, but the core principles of staying safe remain the same. Be skeptical, be cautious, and always trust that gut feeling. The scammers may have fancy new tools, but they’re no match for a smart, savvy person who refuses to be rushed.