
Newsletter Subscribe
Enter your email address below and subscribe to our newsletter
Imagine this: You’re sorting through a loved one’s affairs, a task that’s already emotionally taxing. You’ve handled the paperwork, the phone calls, and the casserole from next door. Now, you need to access their emailEmail, or electronic mail, is a digital communication tool that allows users to send and receive mes... More to find a utility bill. You open their tabletA tablet is a lightweight, portable device with a touchscreen that you can use to browse the interne... More, and it stares back at you, demanding a fingerprint.
Well, that’s a bit of a problem.
Suddenly, you’re not just an heir; you’re a second-rate cyber-sleuth facing a digital Fort Knox. That simple email account is guarded by more security than the gold at, well, Fort Knox.
Welcome to the modern-day inheritance puzzle, where the family jewels are locked behind something called Two-Factor Authentication (2FA) and the only key is your late Uncle Al’s thumbprint.
If you’re facing this digital brick wall, take a deep breath. You’re not the first person to feel like you need a secret decoder ring to handle a digital estate. We’re going to walk through this together, explaining what these security measures are and, more importantly, how you can navigate them without losing your sanity.
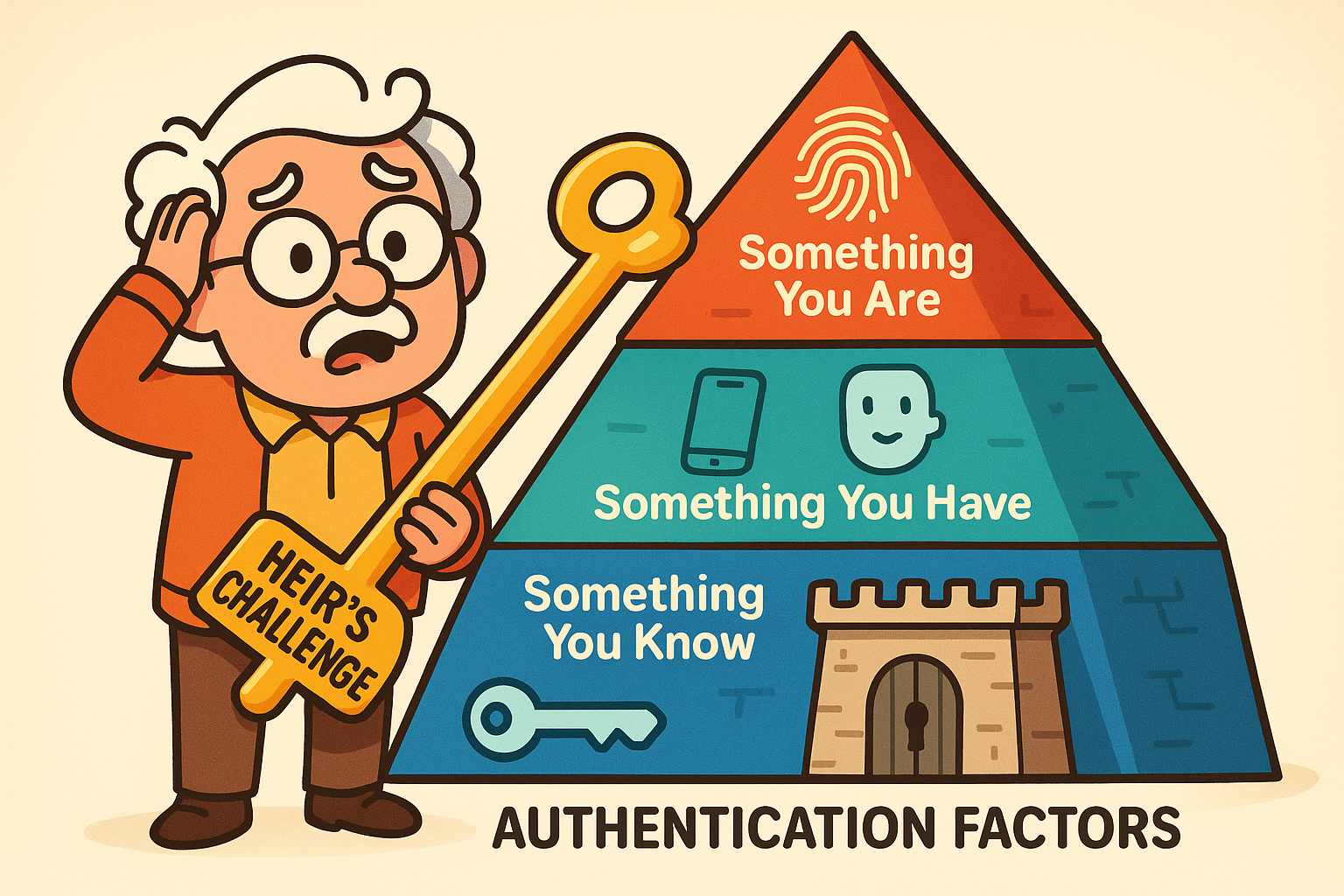
Before we start picking locks (metaphorically, of course!), let’s understand what we’re up against. In the old days, a simple passwordA password is a string of characters used to verify the identity of a user during the authentication... More was enough. But as hackers got sneakier, tech companies added more layers of security, which is great… until you’re the one trying to get in for legitimate reasons.
These layers are based on three types of “factors”:
Two-Factor Authentication (2FA2FA, or Two-Factor Authentication, is a security measure that uses two different types of proof to v... More) just means an account requires two of these factors—usually your password (something you know) and a code sent to your phone (something you have). Multi-Factor Authentication (MFA)Multi-factor Authentication (MFA) is a security feature that adds an extra layer of protection to yo... More is the same idea, just with the potential for even more layers. Understanding the basics of 2FA is crucial, as it’s become the standard for securing important accounts.
BiometricsBiometrics is a way to prove who you are by using something unique about you—like your fingerprint... More (fingerprints, Face ID) use the “something you are” factor. This is where things get particularly tricky for heirs because, unlike a password, you can’t exactly inherit a fingerprint.

The challenge is that these security measures are designed to be personal and non-transferable. They work beautifully to keep criminals out, but they don’t have a plan for what happens when the legitimate owner is no longer around.
Navigating this process while grieving is a monumental task. The key is to work methodically. Your path forward depends entirely on what information you have and what plans, if any, were made beforehand.
When someone sets up 2FA, many services like GoogleGoogle is a multinational technology company known for its internet-related products and services, i... More and Apple provide a set of one-time-use “recovery codes.” Think of these as the “break glass in case of emergency” keys for a digital account.
Some tech companies have started to think about this problem and have created official programs for digital inheritance.
If your loved one set this up, it’s the cleanest and most legally sound way to gain access.
This is the toughest scenario. If a device is locked with a fingerprint or Face ID and you don’t have the passcode, your options are severely limited. Biometric data is non-transferable.
It’s a legal and ethical gray area, but in almost all cases, you cannot compel a company like Apple or Google to unlock a biometrically-sealed device. Attempting to use a deceased person’s biometrics is often technically difficult and legally questionable. Your best bet here is to look for a passcode written down elsewhere or consult a legal professional.
If there was no pre-planning, your final option is to directly contact the service providers (Google, Facebook, the bank, etc.).
You will almost certainly need:
Be prepared for a slow, bureaucratic process. Each company has its own policies, and they are often designed to protect the deceased’s privacy above all else. Patience is your best friend here.
The challenge gets even steeper with specialized assets.
Reading this might have you thinking about your own digital house. How easy would it be for your loved ones to step in if they needed to? Here are a few things you can do right now to make their lives infinitely easier.
This memorable checklist acts as a quick-reference memory anchor for heirs, reinforcing key strategic steps to regain access to accounts with layered security.
This is a classic catch-22. If the codes are trapped on a locked device, they aren’t useful. This highlights the importance of printing physical copies of recovery codes for truly critical accounts and storing them in a safe place.
A death certificate is an official legal document declaring a person’s death. You’ll need to obtain official copies from the vital records office in the county where the death occurred. You will then submit a digital copy or scan of this document to service providers as proof when requesting account access or closure.
Consider involving a lawyer specializing in estate planning if the digital assets are significant (e.g., a business, large financial accounts, cryptocurrency) or if a company is unresponsive to your requests. They can help navigate the legal requirements and issue court orders if necessary.
Dealing with a digital estate is a new and often frustrating challenge, but it’s not impossible. By understanding the locks and knowing which keys to try, you can bring order to the digital chaos and honor your loved one’s legacy. For more tips on navigating the digital world with confidence, explore the resources at Senior Tech Cafe.